P2 Contents Management Software Mac Download
This browser is no longer supported.
Upgrade to Microsoft Border to take advantage of the latest features, security updates, and technical support.
Manual deployment for Microsoft Defender for Endpoint on macOS
Applies to:
- Microsoft Defender for Endpoint Program ane
- Microsoft Defender for Endpoint Plan 2
- Microsoft 365 Defender
Want to experience Defender for Endpoint? Sign up for a free trial.
This topic describes how to deploy Microsoft Defender for Endpoint on macOS manually. A successful deployment requires the completion of all of the following steps:
- Download installation and onboarding packages
- Awarding installation (macOS 10.fifteen)
- Application installation (macOS 11 and newer versions)
- Client configuration
Prerequisites and arrangement requirements
Before you lot get started, meet the main Microsoft Defender for Endpoint on macOS page for a description of prerequisites and system requirements for the current software version.
Download installation and onboarding packages
Download the installation and onboarding packages from Microsoft 365 Defender portal:
-
In Microsoft 365 Defender portal, get to Settings > Endpoints > Device direction > Onboarding.
-
In Section 1 of the page, fix operating system to macOS and Deployment method to Local script.
-
In Section 2 of the page, select Download installation package. Save information technology as wdav.pkg to a local directory.
-
In Section 2 of the page, select Download onboarding package. Save information technology as WindowsDefenderATPOnboardingPackage.zilch to the same directory.
-
From a command prompt, verify that you take the two files.
Application installation (macOS x.15)
To complete this process, you must have admin privileges on the device.
-
Navigate to the downloaded wdav.pkg in Finder and open it.
-
Select Continue, agree with the License terms, and enter the password when prompted.
Important
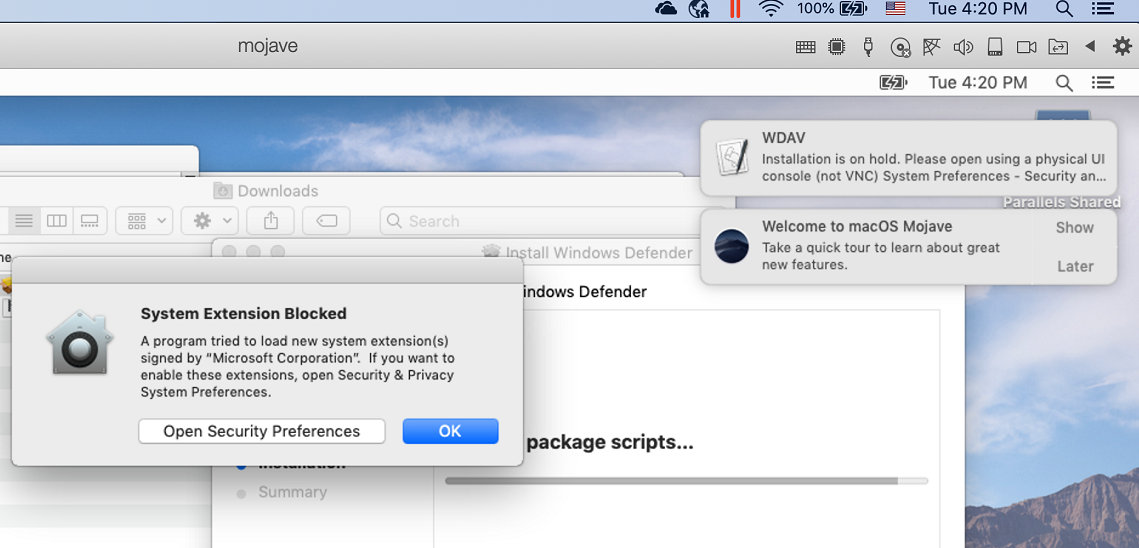
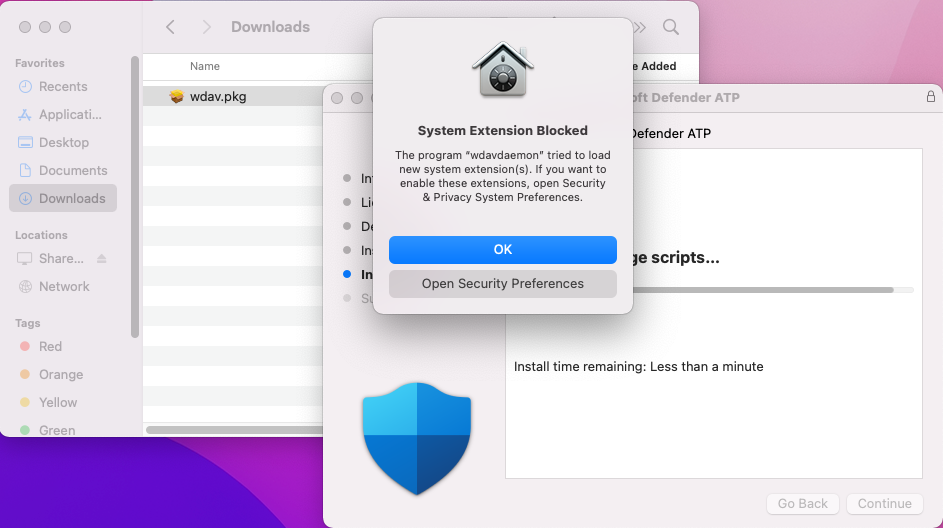
Yous will be prompted to allow a driver from Microsoft to exist installed (either "System Extension Blocked" or "Installation is on hold" or both. The driver must be immune to be installed.
-
Select Open Security Preferences or Open System Preferences > Security & Privacy. Select Allow:
The installation proceeds.
Caution
If you don't select Permit, the installation will proceed subsequently five minutes. Microsoft Defender for Endpoint volition be loaded, but some features, such as real-time protection, volition be disabled. Meet Troubleshoot kernel extension issues for data on how to resolve this.
Notation
macOS may request to reboot the device upon the first installation of Microsoft Defender for Endpoint. Real-time protection will not be available until the device is rebooted.
Application installation (macOS 11 and newer versions)
To complete this procedure, you must have admin privileges on the device.
-
Navigate to the downloaded wdav.pkg in Finder and open it.
-
Select Go on, hold with the License terms, and enter the countersign when prompted.
-
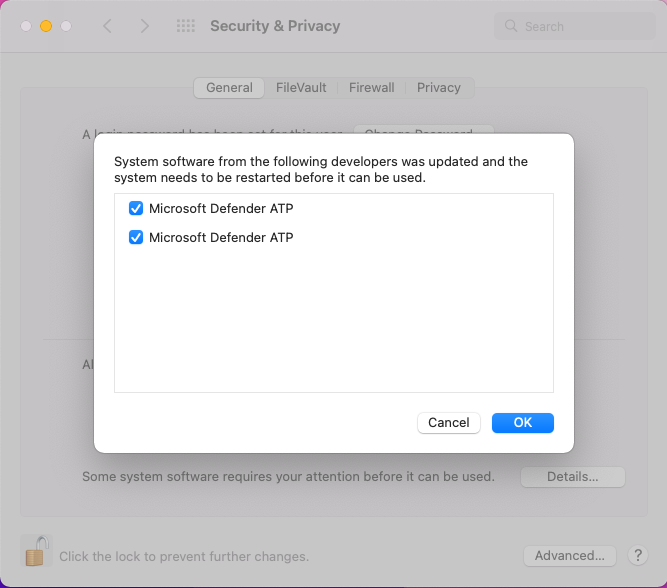
At the finish of the installation process, you'll be promoted to approve the system extensions used by the product. Select Open Security Preferences.
-
From the Security & Privacy window, select Allow.
-
Echo steps 3 & 4 for all system extensions distributed with Microsoft Defender for Endpoint on Mac.
-
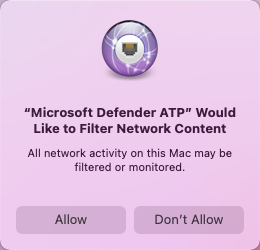
Every bit part of the Endpoint Detection and Response capabilities, Microsoft Defender for Endpoint on Mac inspects socket traffic and reports this information to the Microsoft 365 Defender portal. When prompted to grant Microsoft Defender for Endpoint permissions to filter network traffic, select Allow.
-
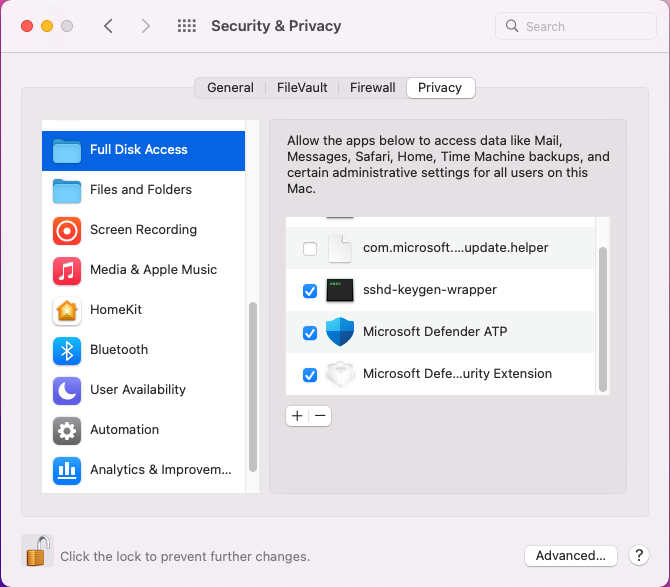
Open System Preferences > Security & Privacy and navigate to the Privacy tab. Grant Full Disk Admission permission to Microsoft Defender and Microsoft Defenders Endpoint Security Extension.
Client configuration
-
Copy wdav.pkg and MicrosoftDefenderATPOnboardingMacOs.py to the device where you deploy Microsoft Defender for Endpoint on macOS.
The client device isn't associated with org_id. Note that the org_id attribute is blank.
mdatp health --field org_id -
Run the Python script to install the configuration file:
/usr/bin/python MicrosoftDefenderATPOnboardingMacOs.py -
Verify that the device is now associated with your organization and reports a valid org ID:
mdatp wellness --field org_idLater on installation, yous'll see the Microsoft Defender icon in the macOS status bar in the top-right corner.
How to Allow Full Disk Access
Circumspection
macOS 10.15 (Catalina) contains new security and privacy enhancements. Beginning with this version, by default, applications are non able to access certain locations on deejay (such equally Documents, Downloads, Desktop, etc.) without explicit consent. In the absence of this consent, Microsoft Defender for Endpoint is not able to fully protect your device.
-
To grant consent, open System Preferences > Security & Privacy > Privacy > Total Deejay Admission. Click the lock icon to make changes (bottom of the dialog box). Select Microsoft Defender for Endpoint.
-
Run an AV detection test to verify that the device is properly onboarded and reporting to the service. Perform the post-obit steps on the newly onboarded device:
-
Ensure that existent-fourth dimension protection is enabled (denoted by a outcome of 1 from running the post-obit command):
mdatp wellness --field real_time_protection_enabled -
Open a Last window. Copy and execute the post-obit command:
curl -o ~/Downloads/eicar.com.txt https://www.eicar.org/download/eicar.com.txt -
The file should accept been quarantined by Defender for Endpoint on Mac. Use the post-obit command to listing all the detected threats:
mdatp threat listing
-
-
Run an EDR detection examination to verify that the device is properly onboarded and reporting to the service. Perform the following steps on the newly onboarded device:
-
In your browser such as Microsoft Edge for Mac or Safari.
-
Download MDATP MacOS DIY.cypher from https://aka.ms/mdatpmacosdiy and extract.
You may exist prompted:
Do you want to let downloads on "mdatpclientanalyzer.blob.core.windows.cyberspace"?
You tin alter which websites tin download files in Websites Preferences.
-
-
Click Allow.
-
Open Downloads.
-
You should run into MDATP MacOS DIY.
Tip
If you lot double-click, you will get the following message:
"MDATP MacOS DIY" cannot be opened because the programmer cannot exist verifier.
macOS cannot verify that this app is free from malware.
[Move to Trash] [Abolish] -
Click Cancel.
-
Correct-click MDATP MacOS DIY, and then click Open.
The system should display the post-obit message:
macOS cannot verify the programmer of MDATP MacOS DIY. Are yous sure you lot want to open information technology?
Past opening this app, y'all volition exist overriding system security which can betrayal your reckoner and personal data to malware that may harm your Mac or compromise your privacy. -
Click Open.
The system should display the following bulletin:
Microsoft Defender for Endpoint - macOS EDR DIY test file
Corresponding alert will be available in the MDATP portal. -
Click Open.
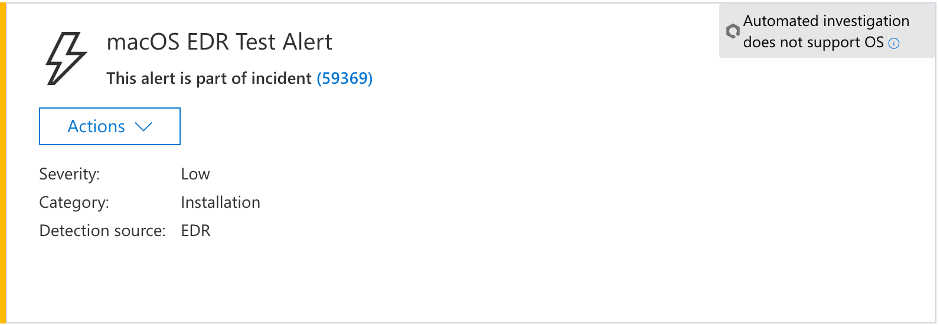
In a few minutes an alert named "macOS EDR Examination Alert" should be raised.
-
Go to Microsoft 365 Defender portal (https://security.microsoft.com/).
-
Become to the Warning Queue.
Look at the alert details and the device timeline, and perform the regular investigation steps.
Logging installation issues
See Logging installation issues for more information on how to find the automatically generated log that is created past the installer when an fault occurs.
Uninstallation
See Uninstalling for details on how to remove Microsoft Defender for Endpoint on macOS from customer devices.
Feedback
Submit and view feedback for
P2 Contents Management Software Mac Download
Posted by: loriallecte.blogspot.com